Henlooo...
In this writeup I will show you a simple vulnerability that I found few days ago on Google Chrome Version 91.0.4472.101 for Linux.
The vulnerability is not remotely exploitable since the attacker needs an access on victim's user credentials and physical access on his device. This kind of issue is not acceptable on Google bug bounty program since physically-local attacks are not in Chrome’s threat model.
I asked my friend for help about this issue and we did some research on it, we tried to exploit the vulnerability to trigger something bigger than HTML Injection but after a long hours of figuring out how to make it a good bug (we aim for RCE), we found nothing.
So I spend hours reading RCE related writeups on the internet and found this cool writeup from Gaurav Mishra which he mentioned the payload he used for his SSRF bug. I tried using his payload and something happened. The browser crashed instantly after the payload executes. I asked my friend if he has a Burp Pro to try using the Burp Collaborator for some SSRF stuff but he said he is also using Burp Community edition. so we ended up reporting this issue instead of continuing the research since also in my mind it will not qualify because as what I have mentioned, it requires access to victim's user credentials and device to reproduce this issue.
--Proof of Concept--
2. Login your account to your Google Chrome account
3. After you login to your account, click your account profile/avatar in the upper right corner of your chrome browser
4. Click the Customize Profile button next to your avatar
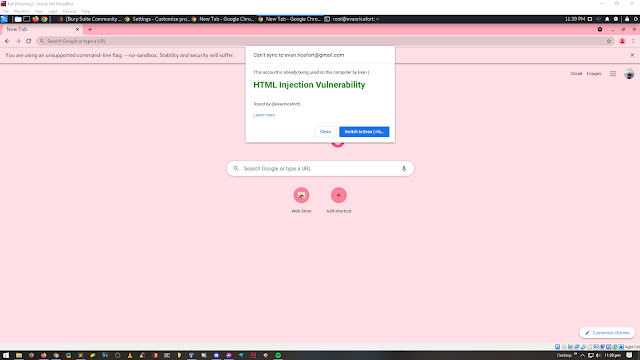
5. Input the payload in the Name your Chrome profile
Payload: ${("".getClass()).forName("java.lang".concat("Runtime")).getMethods()[6].invoke(("".getClass()).forName("java.lang".concat("Runtime"))).exec("wget")}
and this one if you try HTML Injection: <font color="green"><h1>HTML Injection Vulnerability</h1></font><br /><i>found by @evanricafort</i>
6. Now open terminal and type google-chrome or click your profile again in the upper right corner of the browser and then click the + Add button in the Other profile section
7. A new tab will popup and now click + Add
8. Input any name on it and click Done
9. Click the Already a Chrome user? Sign in below the Get Started button
10. Login to your account again (same account you login on step 2) and see the result
FOR CRASHES, PLEASE INCLUDE THE FOLLOWING ADDITIONAL INFORMATION
Type of crash: Browser
Crash State:
root@evanricafort:~# google-chrome
libva error: vaGetDriverNameByIndex() failed with unknown libva error, driver_name = (null)
[36540:36540:0614/235457.931329:ERROR:viz_main_impl.cc(160)] Exiting GPU process due to errors during initialization
[36591:36591:0614/235457.961095:ERROR:gpu_init.cc(440)] Passthrough is not supported, GL is swiftshader
[36510:36510:0614/235528.443094:ERROR:account_info_fetcher.cc(62)] OnGetTokenFailure: Request canceled.
Will not apply HSTS. The HSTS database must be a regular and non-world-writable file.
ERROR: could not open HSTS store at '/root/.wget-hsts'. HSTS will be disabled.
--2021-06-14 23:55:28-- https://clients2.google.com/cr/report
Resolving clients2.google.com (clients2.google.com)... 172.217.161.142, 2404:6800:4005:813::200e
Connecting to clients2.google.com (clients2.google.com)|172.217.161.142|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/plain]
Saving to: ‘/dev/fd/4’
0K 10.9M=0s
Crash dump id: 84b1ebfc0c559df4
2021-06-14 23:55:30 (10.9 MB/s) - ‘/dev/fd/4’ saved [16]
Will not apply HSTS. The HSTS database must be a regular and non-world-writable file.
ERROR: could not open HSTS store at '/root/.wget-hsts'. HSTS will be disabled.
--2021-06-14 23:55:30-- https://clients2.google.com/cr/report
Resolving clients2.google.com (clients2.google.com)... 216.58.220.206, 2404:6800:4005:81b::200e
Connecting to clients2.google.com (clients2.google.com)|216.58.220.206|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/plain]
Saving to: ‘/dev/fd/4’
Crash dump id: ffe8ac349204a557
Illegal instruction
root@evanricafort:~# [0614/235532.220447:ERROR:nacl_helper_linux.cc(307)] NaCl helper process running without a sandbox!
Most likely you need to configure your SUID sandbox correctly
An attacker must have access to the user's browser to modify a profile name. I don't think this is a security issue since this bug cannot be exploited remotely. Physically-local attacks are not in Chrome’s threat model [1].This issue still needs to be fixed, though. I'll look into escaping the profile name before displaying it in web contents.
So that is all for this writeup. Stay safe and happy hacking everyone!
No comments:
Post a Comment